SQL Server database and security
In this option, there are now two connection files, one to replace the Microsoft Access security file and one to replace the Microsoft Access database. There is a server to hold the SQL Server databases that contain the security data and the main database.
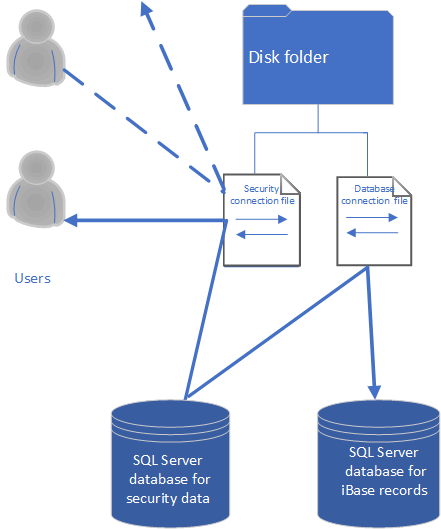
Of the three options, this is the most secure configuration. However, from the user’s point of
view nothing has changed, because they see connection files that appear to be a security file and
database. The points to remember are still:
- Users gain access to databases through the security file regardless of its file type.
- A security file can control access to several databases regardless of their file type.
- Each database has just one security file associated with it regardless of its file type.
- There is a server running SQL Server, with consequent changes in performance and administration.
- There is an opportunity to centralize the operation and administration of multiple databases, and automate more of the routine administration.
- There is an opportunity to operate another level of security between the user and the data.
- There is an opportunity to use replication to distribute copies of iBase data and database objects between servers and keep these synchronized.
