Microsoft Access
The simplest possible arrangement is to have one security file and one database file held in a disk folder, typically shared to network users. The diagram shows two users: the upper one able to read and write data to the database, the lower one denied all access to the database.
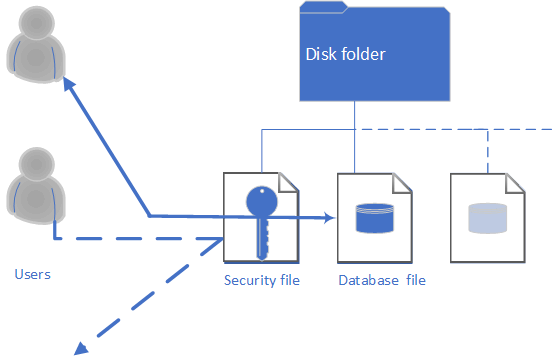
The important points to remember are:
- Users gain access to databases through the security file, by logging on with an appropriate user name and password.
- A security file can control access to several databases.
- Each database is associated with just one security file.
- Each database records which security file is used to access it.
This simple configuration can be extended in several ways: by adding many databases, by adding more users, and by allowing those users different degrees of access to the databases ranging from full administration rights, through varying levels of ability to change or inspect data, down to no access at all.
It is also possible to create additional security files for other databases provided the security files are in separate folders.
