Project management
The following section introduces the different steps that are involved in deploying iBase database replication. It brings together the preparation that is required for the iBase security file, the database, and the audit log with the configuration required in SQL Server.
Users can work in the database that becomes the publication database, even if it is not yet configured for replication. Users at the subscriber sites can only start work after replication is fully configured.
Version 5 security files and databases require upgrading to version 8, and after these files are upgraded, they cannot be used with iBase 5. You must also convert (upsize) the security file to SQL Server format (and the database if it is in Microsoft Access format). You can only replicate SQL Server databases.
The following flow charts show the sequence in which the configuration tasks can be completed, who performs these tasks (whether the iBase or the SQL Server administrator) and what the dependencies are.
For more background information on managing the deployment of iBase database replication, see:
New systems or systems with small amounts of data
The following flow chart shows the sequence of tasks and the dependencies when you are configuring a new system or a system in which the initial snapshot of data, for the iBase database containing the entity and link data, is small enough to transfer over a communications link.
The following flow chart shows, for example, that an SQL Server administrator might configure the publications and subscriptions at the same time if the preparation of the iBase security file and database is complete.
The work flow is identical for all supported versions of SQL Server.
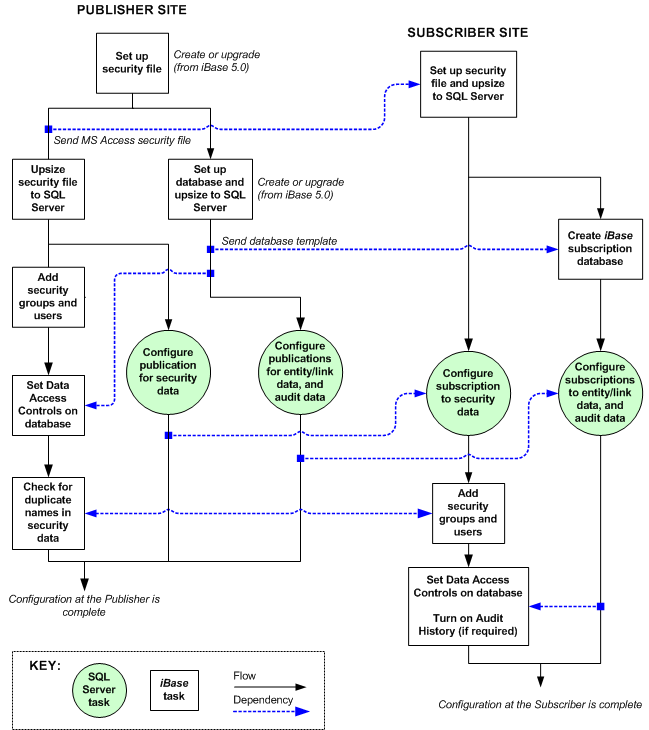
Further information
Publisher site: iBase administrators
Publisher site: SQL Server administrators
Subscriber site: iBase administrators
Subscriber sites: SQL Server administrators
Systems with large amounts of data
The following flow chart shows the sequence of tasks and the dependencies when you are configuring a system in which the initial snapshot of data, for the database containing the entity and link data, is too large to transfer over a communications link.
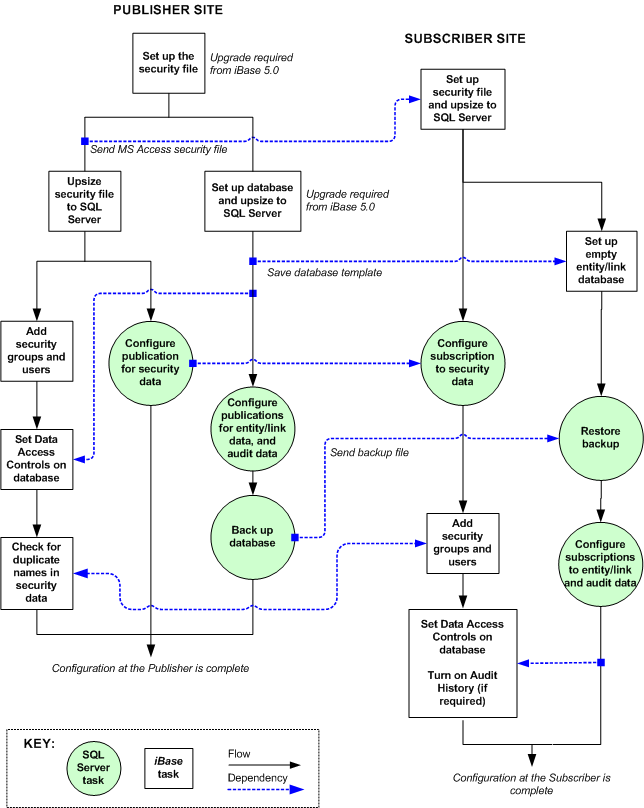
Further information
Publisher site: iBase administrators
Publisher site: SQL Server administrators
Subscriber site: iBase administrators
Subscriber sites: SQL Server administrators
