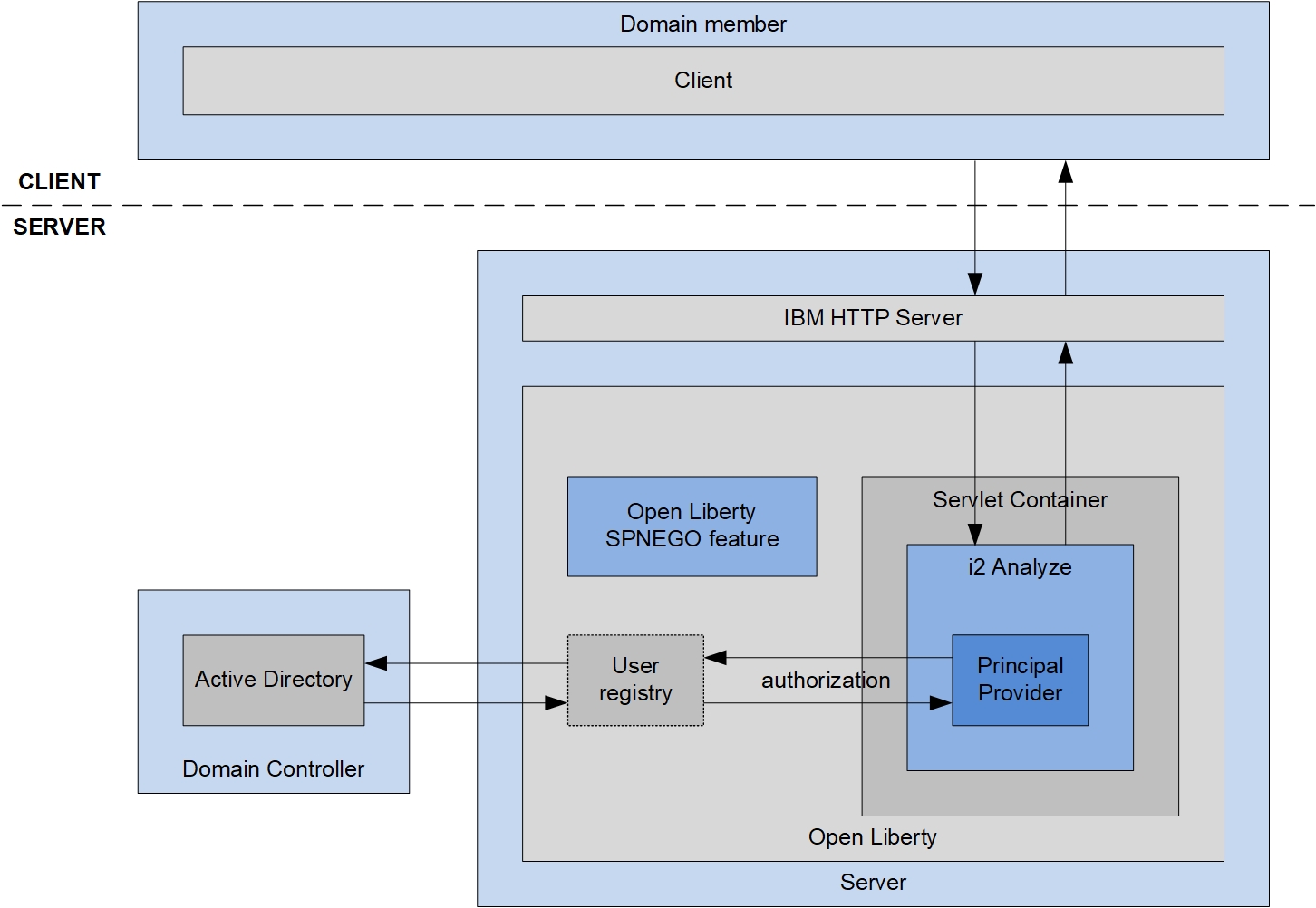
i2 Analyze with SPNEGO single sign-on model
Configuring i2 Analyze to use SPNEGO single sign-on changes the way that users authenticate with the platform. A deployment that uses SPNEGO single sign-on requires the user to access i2 Analyze on a workstation that is a member of the same domain as i2 Analyze.
Authentication
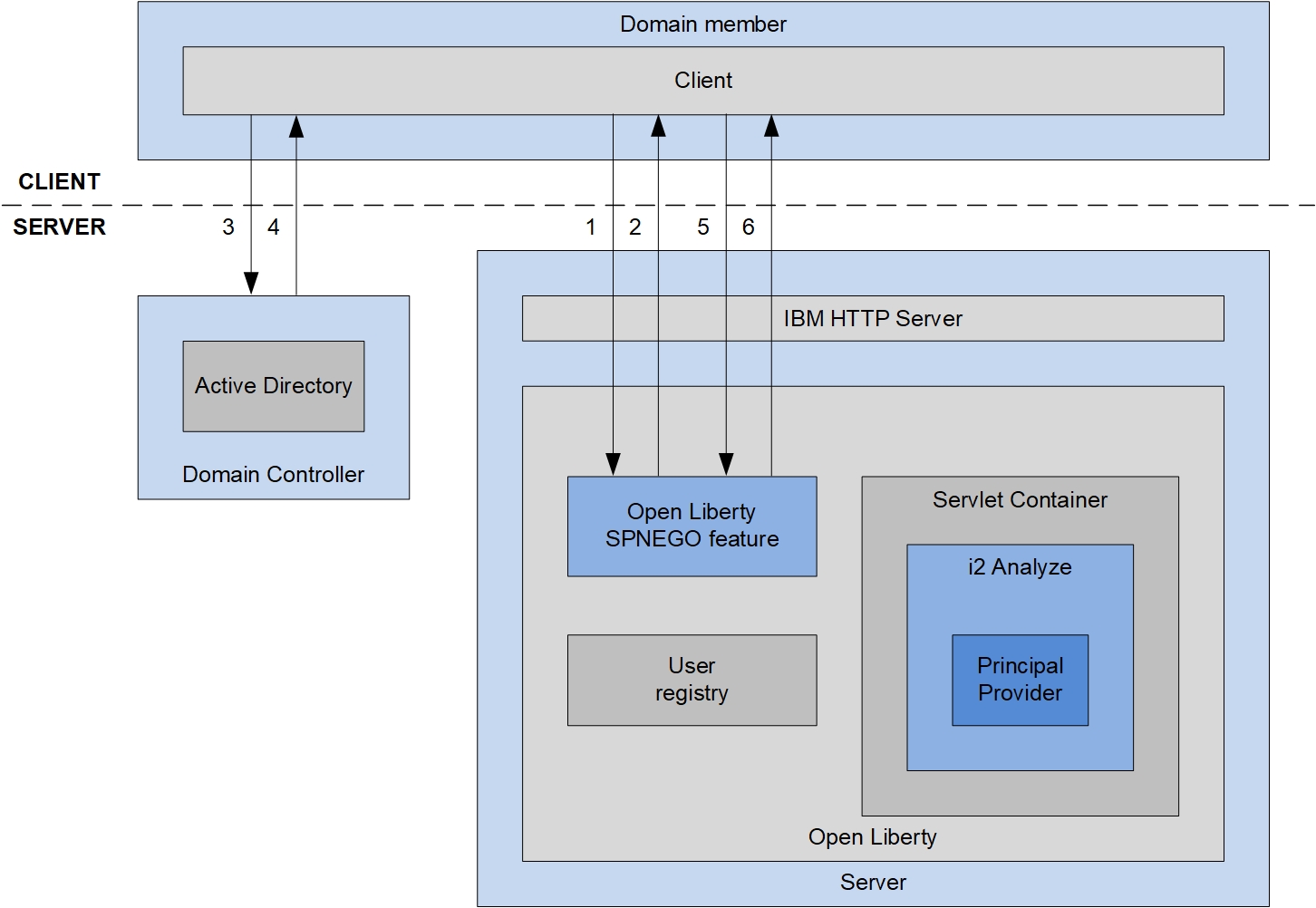
When i2 Analyze is configured to use SPNEGO single sign-on, the authentication sequence between the client and the platform matches the following steps and the associated diagram:
- The client attempts to connect to WebSphere Application Server Liberty profile with an
HTTP/Post/Getrequest. - WebSphere Application Server Liberty profile returns
HTTP 401with aNegotiateheader. - The client requests a SPNEGO token from the domain controller.
- The domain controller returns a SPNEGO token to the client.
- The client attempts to connect to WebSphere Application Server Liberty profile with an
HTTP/Post/Getrequest and the SPNEGO token. - On successful authentication, the client receives a Lightweight Third-Party Authentication (LTPA) token in a cookie. During normal operation, the client passes the cookie back to i2 Analyze.
Authorization
After the user is authenticated, they are logged in to i2 Analyze. To define the data that the user has access to, the user must be authorized by i2 Analyze.
For authorization, the i2 Analyze application communicates with Active Directory, through the WebSphere Application Server Liberty profile user registry APIs to retrieve information about the current user. The principal provider then maps the retrieved information to security dimension values in the i2 Analyze security schema.